
Security Risk Assessment - An Unavoidable Check for Businesses
When encountering a natural or man-made disaster, organizations' existing IT security controls play the most crucial part. Businesses focusing less...
Learn More
In an era of interconnected technologies, the digital landscape presents both unprecedented opportunities and formidable challenges. As organizations readily adapt to cyberspace, virtual technologies, and cloud security solutions, the threat landscape appears to expand concurrently. Data breaches, identity theft, ransomware attacks, phishing, and other potential risks can massively impact individuals and organizations alike.
To address increasing vulnerabilities and cyber risks, developing and implementing an effective cybersecurity strategy is paramount for businesses. They can achieve this by actively identifying and comprehending the vulnerabilities of their IT infrastructures, networks, and servers. Furthermore, cybersecurity awareness training also educates and empowers individuals to understand and prevent potential digital risks.
This guide sheds light on the top 10 cybersecurity controls every business should know.
Cybersecurity breaches, ranging from data theft to intricate ransomware attacks, exploit vulnerabilities in businesses’ interconnected systems. The urgency to fortify your digital defenses has never been more critical. To effectively navigate this complex cyberspace, businesses must actively implement robust cybersecurity controls.
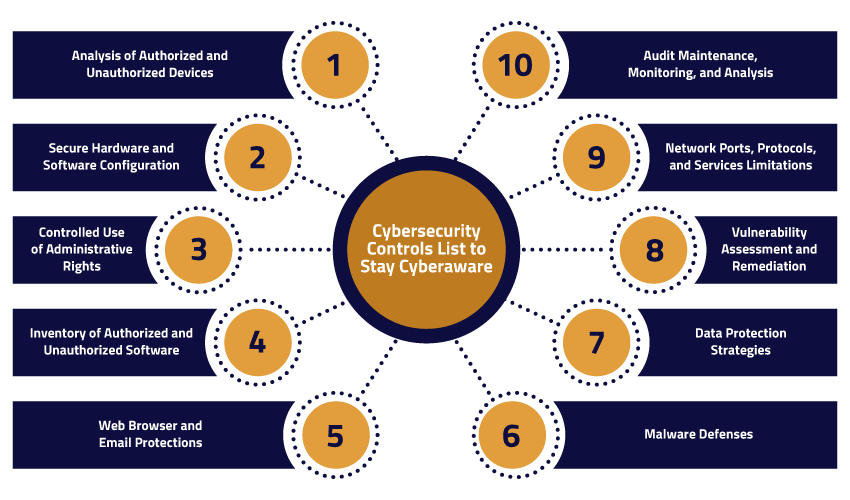
Read along and discover the must-have cybersecurity controls for your business to stay cyber-aware and digitally secure.
Securing any digital frontier begins with acquiring comprehensive information on all devices connected to your business’s network, both authorized and unauthorized. This includes computers, servers, mobile devices, and any other endpoints. By maintaining an up-to-date analysis, you can identify and manage potential security risks associated with each device more effectively. Additionally, regular audits ensure that only authorized devices have access to the network, significantly reducing the likelihood of external threats.
Securing all devices and software through robust configuration stands as the second vital control. This proactive approach significantly mitigates the risk of breaches and exploitation. This involves implementing a baseline of security settings for operating systems, applications, and hardware components.
Moreover, leveraging the power of automated tools fueled by ML, deep learning, and others, you can securely configure mobiles, laptops, workstations, servers, networks, and other components. By adhering to this cybersecurity control, you can minimize the attacks and reduce the risk of exploitation.
Administrative controls, while essential for business operations, pose a significant risk as they grant individuals access to critical systems, networks, and confidential information. This elevated access presents a prime opportunity for cybercriminals, who can exploit it to compromise entire businesses and sell sensitive data on the dark web for substantial profit.
Controlling and monitoring the use of these privileges is crucial for preventing unauthorized access and limiting the impact of potential security incidents. The principle of least privilege should be applied, ensuring that users only have the permissions necessary to perform their job functions. Regularly reviewing and updating access permissions helps prevent misuse and reduces the risk of insider threats.
Similar to hardware, maintaining authorized and unauthorized software inventory is equally crucial cyber security control for businesses to maintain cybersecurity. You should keep track of all installed software, including operating systems, applications, and utilities. This control helps in identifying and removing any unauthorized or vulnerable software that may pose a security risk. Furthermore, Regular updates and patches should be applied to mitigate known vulnerabilities in the authorized software.
Email and web browsers are common entry points for external cyber risks such as malware, social engineering, and phishing attacks. Implementing strong email and web browser controls is essential for preventing these threats from jeopardizing your business and its IT systems. This includes filtering and scanning email attachments, monitoring for malicious links, and educating users about safe browsing practices.
Regular training and awareness programs can empower individuals to recognize and avoid potential threats in their email and web interactions.
Viruses, ransomware, and other malicious software infiltration form the basis for the wider malware attacks. Considering a significant threat to cybersecurity controls, you should integrate proactive defense mechanisms to counter these infiltrations. Implementing robust malware defense involves deploying antivirus and anti-malware solutions across all endpoints.
An effective defense strategy relies heavily on three key components: regularly updating signatures, utilizing behavior-based detection mechanisms, and conducting frequent scans.
Protecting sensitive data is a cornerstone of cybersecurity and implementing encryption, both in transit and at rest, safeguards information from unauthorized access. Classify data based on its sensitivity and apply appropriate access controls, ensuring compliance with regulatory requirements and alignment with industry best practices. Regularly backing up data and testing restoration procedures further strengthen security against breaches and data loss.
The ever-evolving external threats necessitate the implementation of robust cybersecurity controls for effective countermeasures and prevention strategies. Conducting continuous vulnerability assessments empowers you to identify and address potential weaknesses in your systems promptly.
Upon identification of vulnerabilities, a systematic remediation process should be established to patch or mitigate the associated risks proactively. Regular software updates, timely application of security patches, and vigilant monitoring for emerging threats are fundamental elements of an effective vulnerability management program.
Controlling network ports and protocols helps businesses manage and reduce potential cybersecurity and unauthorized access risks. Unnecessary ports and services should be disabled, and only those essential for business operations should remain active. For enhanced security, you should also integrate firewalls and intrusion detection/prevention systems to monitor and control network traffic.
Audit logs analysis is last in this list of top 10 cybersecurity controls. It provides a valuable source of information for detecting and investigating security incidents. You should implement robust logging mechanisms across the systems and networks. Regularly reviewing and analyzing audit logs can help identify suspicious activities, unauthorized access attempts, or potential security breaches.
Automated tools can aid in the monitoring process, alerting security teams to identify anomalies that may require further investigation.
Technological transformation results in dependence of every business on automated, efficient, and self-driven practices. However, this also contributes to increasing cyber risks. The top 10 controls discussed in this guide provide a comprehensive framework for individuals and organizations to enhance their cybersecurity posture. Implementing these controls, regularly updating them, and staying informed about emerging threats can collectively create a more secure digital environment for everyone.
Ferro Technics is an emerging IT Security, network and infrastructure certifications leader offering recognized and bespoke cybersecurity courses. Our training programs are approved by the EC Council, PECB, ISACA, and other accrediting authorities. In addition to ethical hacking mastery, network security practices, and governance expertise, we also provide consultation and assistance to businesses in implementing cybersecurity controls.
To further assist businesses in fortifying their digital frontiers, we offer cybersecurity consulting services where our seasoned professionals critically evaluate IT infrastructure maturity, identify vulnerabilities, and devise proactive strategies aligned with business goals.
Contact Us Today and Experience How We Can Help Strengthen Your Organization’s Information Security System

When encountering a natural or man-made disaster, organizations' existing IT security controls play the most crucial part. Businesses focusing less...
Learn More
On average, around 2,200 cyberattacks are launched every day. The increased usage of cloud solutions, third-party transactions, and overall digitiz...
Learn More
In the current era of advanced technology, where cyber-criminals and hackers are finding new ways to infiltrate systems and steal sensitive data, e...
Learn More
In the rapidly evolving digital landscape where advanced technologies such as Artificial Intelligence (AI), Deep Learning, Machine Learning (ML), B...
Learn More
The results of a joint study by Jeff Hancock (Professor at Stanford University) and Tessian, a security company, show that human error or employee ...
Learn More
The cybersecurity industry has recently undergone rapid growth and global-level expansion like no other sector, estimated to grow from $190.5 billi...
Learn More
The digital age has significantly increased the challenge of m...
Learn More
Our digital world is a double-edged sword. While it offers incredible opportunities, it also exposes us to unseen dangers. Cybersecurity fundamenta...
Learn More
Vulnerability assessment is the systematic review of network ...
Learn More
In the dynamic and constantly evolving field of cybersecurity, maintaining a proactive stance against emerging threats necessitates a comprehensive...
Learn More
Obtaining industry-recognized certifications is a powerful way to showcase your expertise, enhance your credibility, and unlock new caree...
Learn More
In today’s digitally-driven world, cybersecurity has become a critical component for organizations across all sectors. The growing ...
Learn More
Have you ever wondered how you can become a cybersecurity expert and significantly advance your career? If yes, ...
Learn More